How to check if your Linkedin password has been stolen
There are two multiple ways of checking your linkedin password hash. Here, I am focusing on two ways of searching your password hash via different leaks available online.
1. Combo_not.zip via Python script
The passwords were uploaded online in a 270mb text file via https://disk.yandex.net .(Mirrors pastebin.com or pastie.org ) You can check if your password is in that list by first creating your password in SHA-1 format and then check the txt file for it.
Pastebin Download Page
 |
| Pastebin mirror page for Linkedin dump |
Pastie Download Page
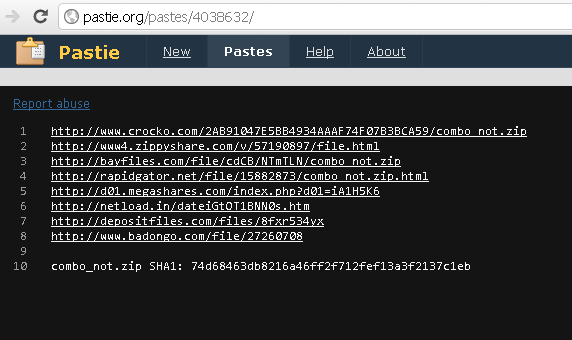 |
| Pastie mirror page for Linkedin dump |
After downloading combo_not.zip please extract the combo_not.zip and you will find out combo_not.txt file which need to be further analyzed for your password offline.
A python script is available online for converting your password into sha1 hash and search combo_not.txt for your sha1 hash match. You will need python interpreter for running above python script. The source code of python script is following.
"""
Save this file as linkedin_hash.py and ensure it's
in the same folder as combo_not.txt
"""
from hashlib import sha1
import sys
password = sys.argv[1]
hsh = sha1(password).hexdigest()
x = 0
for line in open('combo_not.txt','r'):
if hsh == line.strip():
x += 1
elif "00000" + hsh[5:] == line.strip():
x += 1
print "Number of matches: %d" % x
Now execute the program by typing python linkedin_hash.py password. Replace the parameter with your password. This will show you exact result of your password.
2. 'Linkedin SHA1 Passwords' Torrent and PHP
First download the linkedin password hash torrent and extract the archive. After extracting archive please ensure that you have PHP cli and grep is installed on the system.
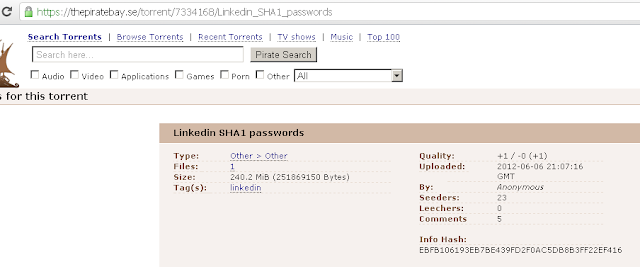 |
| thepiratebay Linkedin SHA1 passwords |
For Linux Systems
Run
php -r 'echo sha1("password") . "\n";'
This will generate your sha1 password hash. Now we have to find our password hash from the give dump.
Run
grep 'your sha1_hash' sha1.txt
For Windows Systems
Run
E:\Downloads\xampp\php>php -a
Interactive mode enabled
<?php
echo sha1("linkedin");
?>7728240c80b6bfd450849405e8500d6d207783b6^C
E:\Downloads\xampp\php>
E:\Downloads\xampp\php>grep "7728240c80b6bfd450849405e8500d6d207783b6" combo_not
.txt
//Convert first five bytes into 0 and bingo
E:\Downloads\xampp\php>grep "0000040c80b6bfd450849405e8500d6d207783b6" combo_not
.txt
0000040c80b6bfd450849405e8500d6d207783b6
E:\Downloads\xampp\php>
For Windows Systems
Run
E:\Downloads\xampp\php>php -a
Interactive mode enabled
<?php
echo sha1("linkedin");
?>7728240c80b6bfd450849405e8500d6d207783b6^C
E:\Downloads\xampp\php>
Now run grep
E:\Downloads\xampp\php>grep "7728240c80b6bfd450849405e8500d6d207783b6" combo_not
.txt
//Convert first five bytes into 0 and bingo
E:\Downloads\xampp\php>grep "0000040c80b6bfd450849405e8500d6d207783b6" combo_not
.txt
0000040c80b6bfd450849405e8500d6d207783b6
E:\Downloads\xampp\php>
Linkedin saved sha1 password unsalted which makes russians to break easily. Hope we all have to learn from above hack.
Thanks
Bhokaldied